Managing a domain and web hosting account might seem routine, but security lapses in this space can have devastating consequences. From simple misconfigurations on a server to sophisticated registrar-level attacks, flaws in domain hosting setups have enabled data breaches, brand impersonation, and downtime for businesses of all sizes. In this article we examine the most common hosting-related vulnerabilities – including server misconfigurations, domain hijacking schemes, DNS-level attacks, SSL/TLS issues, and weak hosting credentials – and illustrate each with real-world examples and expert findings. Along the way we suggest where charts or flowcharts could help visualize key trends (for instance, a pie chart of misconfiguration types or a timeline of hijacking incidents). We end with a practical checklist of best practices for secure domain hosting.
Server Misconfigurations: Open Doors for Attackers
One of the top cybersecurity hazards in web infrastructure is misconfiguration of servers and services. In the 2021 OWASP Top 10, “Security Misconfiguration” ranked among the most critical weaknesses, with over 90% of applications found to have some insecure default setting. Security researchers similarly warn that roughly 73% of organizations suffer at least one critical security misconfiguration in their tech stack. Common examples include leaving default admin accounts or passwords unchanged, shipping with verbose error messages or sample applications, and failing to disable unnecessary services. For instance, a server that still has the default “tomcat admin/admin” login, or one that exposes stack traces to the web, gives attackers an immediate inroad.
Specific misconfigurations frequently seen on web servers include unintended directory listings and overly broad file permissions. If “directory browsing” is left enabled on a public webroot, anyone can traverse folders and download files that were meant to be hidden. In one security write-up, disabling directory listings was highlighted as essential; leaving it on lets attackers download compiled classes or view code, potentially exposing sensitive logic to reverse engineering. Similarly, Unix file permissions are often mis-set so loosely that any local user (or even the web process itself) can read or overwrite critical files, or traverse between virtual hosts. Default nginx or Apache configurations may leave an index.html placeholder or an “It works!” page open, betraying the underlying server software and version. In short, anything left at a non-secure default setting can be an easy target.
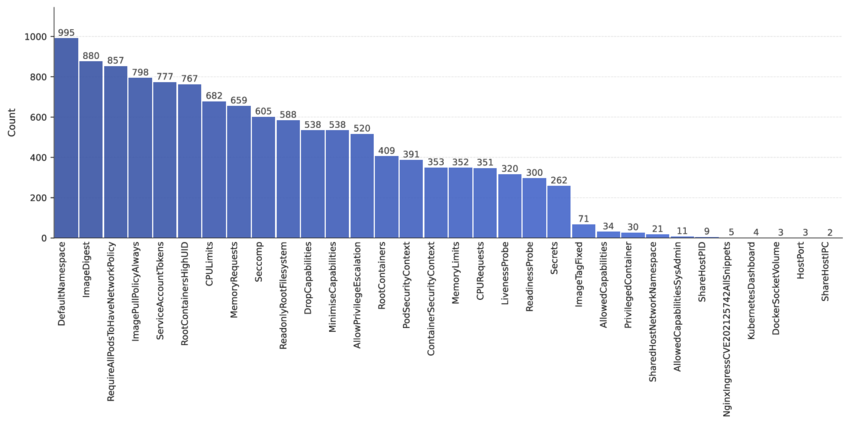
A useful way to visualize these risks would be a pie chart breaking down the most common misconfigurations (e.g. unpatched software, open directory listings, default credentials, excessive permissions, etc.). For example, industry surveys often find that missing patches and default admin accounts make up a large slice of all misconfig bugs. Administrators should regularly audit their web servers (including NGINX/Apache configs, cloud instance rules, and container settings) to ensure directory listing is disabled, sample/demo pages are removed, and only minimal services and ports are exposed. Automating configuration checks and hardening (for instance via Ansible or Puppet) can also close many of these gaps.
Domain Hijacking: Stealing Your Online Identity
Perhaps the most alarming hosting flaw is domain hijacking, where an attacker takes control of a domain name itself, redirecting all its traffic (and email) to an attacker-controlled system. This can be done by tricking the domain registrar, compromising DNS settings, or other tricks. When a domain is hijacked, the attacker effectively owns your brand online – they can replace your website with phishing pages, harvest customer credentials, intercept sensitive emails, and destroy trust. For example, in one high-profile case a popular Minecraft community (Hypixel Network, with 10+ million users) had its domain stolen in May 2022. The hijackers immediately posted a fake cancellation announcement (with a cryptocurrency scam link), sowing panic among users. Such incidents show that even major companies can fall victim, often with devastating reputational fallout.
In recent years, domain hijacking attacks have surged, partly due to a technique nicknamed “Sitting Ducks.” As reported by Infoblox and The Hacker News, attackers have exploited DNS misconfigurations to seize control of tens of thousands of domains. In one study, Infoblox scanned three months of data and found ~800,000 domains with risky configurations; about 9% (≈70,000) of them were subsequently hijacked. The “Sitting Ducks” vector works when a domain’s authoritative DNS is delegated to a provider separate from its registrar. If that delegation is “lame” (meaning the registrar doesn’t strictly verify that delegation), a criminal can “claim” the domain at the DNS provider without logging into the original registrar account. In plain terms: the attacker finds a domain whose DNS is pointing off to a third-party hosting service, then registers a (free) account on that DNS service using the same domain name. Because the DNS records were not locked at the registrar, the attacker can then set malicious IP addresses and subdomains, all while the legitimate owner remains oblivious.
In practice, hijackers have used these stolen domains for phishing and fraud. Infoblox noted that even well-known brands, nonprofits, and government domains fell prey, and threat groups recycled hijacked domains in “rotational” attacks (one attacker holds a domain briefly, then abandons it and another attacker grabs it). Phishing campaigns under the hijacked domains mimic legitimate services (e.g. shipping confirmations, tech support sites), tricking recipients because the domain matches the brand. In many cases, the only sign of compromise is an unexplained change of the domain’s IP address. If one were to illustrate this, a flowchart could show the domain hijacking process: starting with reconnaissance (finding domains with loose delegations), through phishing the registrar or creating a malicious DNS account, to final steps where DNS records are altered for exploitation. Using such visual aids can help administrators understand how simple mistakes in DNS delegation or registrar verification pave the way for takeover.
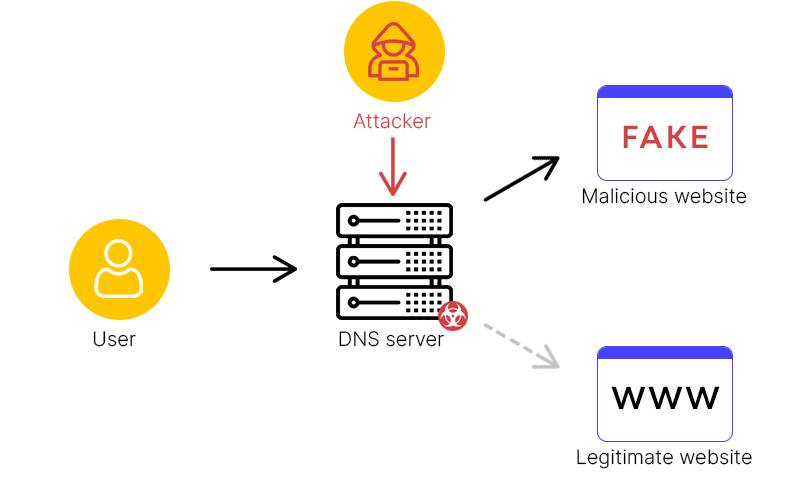
DNS Vulnerabilities: Spoofing and Cache Poisoning
The Domain Name System (DNS) – essentially the Internet’s phonebook – is itself a source of vulnerabilities when misused. DNS spoofing (also called DNS cache poisoning) is a technique where an attacker feeds false DNS responses to a resolver, causing users to be directed to malicious sites. At its core, DNS cache poisoning “injects forged answers into the DNS resolver cache, causing the server to direct users who enter a domain to incorrect IP addresses, potentially leading them to malicious websites without their knowledge”. Famous examples include the 2008 Kaminsky attack (exploiting DNS transaction IDs) and various cache-skimming exploits. More recently, researchers revealed “MaginotDNS,” a sophisticated poisoning attack (presented at Black Hat 2023) that could compromise entire top-level domains by abusing inconsistencies in DNS software. MaginotDNS was possible because roughly one-third of major DNS servers still had weak checks, but fortunately fixes have been patched since then.
Even without advanced attacks like MaginotDNS, everyday DNS misconfigurations can create risk. For example, forgetting to enable DNSSEC (security extensions) means responses are unauthenticated, so on-path attackers or even malicious home routers can replace DNS replies. Typosquatting is another DNS trick: if an organization registers too many TLD variants (e.g. .net, .org) or subdomains without strict lock, an attacker might snag an expired variant and pretend to be the brand. One could imagine a chart here of reported DNS attacks over time – perhaps a rising line graph of phishing sites tied to DNS spoofing. In practice, organizations should lock down who can update their DNS zones (using registrar locks and DNSSEC), closely monitor any zone-change logs, and use secure resolvers (like DNS-over-HTTPS/TLS) to reduce the chance of spoofing.
SSL/TLS Issues: Expired and Misissued Certificates
Websites rely on SSL/TLS certificates to encrypt traffic and authenticate identity. However, certificate mishaps abound. The simplest failure is letting a certificate expire – when this happens, browsers will warn users that the site is insecure or inaccessible. Such outages have occurred at major companies: for instance, a big cloud provider once accidentally let an internal certificate expire, causing services to break until it was manually renewed. Behind the scenes, improper renewal scripts or neglected automation can leave sites vulnerable to “man-in-the-middle” if a user ignores the warning and proceeds to an unencrypted connection.
A more insidious problem is misissued certificates. Certificate Authorities (CAs) have occasionally issued rogue certs by mistake or under duress. The most infamous case was the 2011 DigiNotar breach: Dutch CA DigiNotar was hacked and ended up issuing hundreds of fraudulent certificates, some of which were used to intercept Gmail accounts in Iran. In general, an academic study of 1,300+ misissuance incidents found that software bugs and policy misinterpretations at CAs cause about 42% of these problems. In other words, even the trust layer can fail due to human or technical error. In the age of short-lived certs (like Let’s Encrypt’s 90-day model), many organizations automate renewals – a good practice – but one must also watch for CA outages or configuration mistakes. A recommended mitigation is to use certificate transparency logs and monitoring so that unexpected or duplicated certificates for your domain can be detected. A visual here might be a pie chart of TLS failures (e.g. “expired,” “revoked,” “mismatched CA,” etc.), highlighting how misconfiguration often shows up as expiration errors or chain trust issues. By promptly updating certs, using strong cipher suites, and employing automation and logging, most SSL/TLS issues can be prevented.
Hosting Provider Weaknesses
Not all security flaws lie with the customer; hosting providers themselves can introduce risks through insecure defaults or poor isolation. In shared hosting environments, for example, if one tenant’s virtual site is compromised (say by an exploited plugin in WordPress), the attacker may be able to climb to the hosting control panel or neighboring accounts if the provider hasn’t properly containerized each user. There have been cases where a single vulnerable app on a shared server allowed an attacker to scan and reach other customers’ files on the same machine. Other provider-side issues include default administrative ports left open (e.g. SSH without key authentication), outdated control panel software, or lack of network segmentation. Even reputable hosts can slip: for instance, a popular hosting service once had a vulnerability that leaked customer database credentials due to a mis-set configuration file.
Often, the warning signs are hidden behind vendor marketing. A site hosting 100+ customer websites might advertise “all sites on our servers are completely isolated,” but unless audited, you can’t be sure. Thus, organizations should check their provider’s security features: Do they offer firewalls, DDoS protection, or VPC/VLAN segmentation? Can customers change default settings (e.g. close unneeded ports)? Using multi-tenant Docker containers or separate virtual machines for each site is safer than plain shared Apache instances. In short, when evaluating a host, assume the worst – that a breach in one account can affect others – and look for explicit support for isolation and frequent system updates. A useful chart might compare “hosting risks” (e.g. shared-site compromise vs. dedicated server management) to guide such choices.
Poor Credential Management
Even with lock-tight technology, human factors often undermine security. Poor credentials – whether for the hosting control panel, domain registrar account, FTP services, or DNS management – can hand victory to attackers. Common pitfalls include password reuse (using the same password for email, hosting, and registrar), lack of multi-factor authentication (MFA), and failure to rotate keys or API secrets. In a typical domain takeover, “the attack often starts with something as simple as a phishing email to your domain administrator or a compromised account at your domain registrar”. For example, if an attacker tricks an employee into giving up the registrar login, they can instantly point the domain elsewhere or even transfer it to a new owner. The Valimail guide on domain theft describes exactly such a scenario, warning that once attackers have a registrar control panel login, they can redirect your domain to any site they want.
Real incidents underscore this risk. In May 2022, the Hypixel example cited above was believed to have started with a leaked or phished credential somewhere in the chain. Similarly, the “Sitting Ducks” hijacks rely on an attacker creating or accessing an account at the DNS provider side – often by registering with the same domain name and zero verification by the registrar. Companies frequently publish security bulletins about stolen API keys or leaked SFTP passwords leading to site breaches. A helpful visualization here could be a bar chart of breach causes (phishing vs. brute force vs. credential stuffing), highlighting that credential theft is far and away a top vector. The remedy is straightforward (though sometimes hard to enforce): use unique, complex passwords; enable MFA on all hosting and registrar accounts; require hardware keys if possible; and monitor for unusual login attempts or new device approvals. Registrars and hosts often offer “domain lock” or notifications on any account changes – these should be turned on by default. With proper authentication hygiene, many hijacking attempts can be stopped at the door.
Practical Checklist for Secure Domain Hosting
- Harden Server Configurations: Disable directory listings, remove sample pages, and ensure only necessary services and ports are active. Regularly apply OS and app patches.
- Secure Default Settings: Change any default administrator logins and passwords (for NGINX, cPanel, databases, etc.) and disable or remove unused accounts.
- Lock and Monitor DNS Delegations: Use registrar locks on your domain, implement DNSSEC where possible, and confirm that your authoritative DNS provider matches the registrar’s records. Set alerts for any unexpected DNS zone changes.
- Enable Two-Factor Authentication: Require MFA on all critical accounts (domain registrar, hosting control panel, email admin). Avoid relying solely on emailed reset links or SMS verification.
- Automate Certificate Management: Use tools like Let’s Encrypt or enterprise certificate managers to renew SSL/TLS certificates before they expire. Monitor certificate transparency logs to detect any misissued or rogue certs.
- Audit Hosting Isolation: If on shared hosting, inquire about tenant separation (containers, virtual machines). Consider dedicated or VPS hosting if isolation is insufficient. Keep third-party plugins and CMS platforms up to date.
- Use Strong, Unique Credentials: Never reuse passwords across services. Employ a password manager and rotate keys or passwords periodically. Avoid storing unencrypted secrets in code or repositories.
- Regularly Review Logs: Check access and error logs on your web server, DNS server, and registrar account for anomalies, such as unfamiliar IP logins or configuration changes.
- Educate the Team: Train staff on phishing and social engineering. Ensure domain and DNS ownership is understood by multiple trusted persons (to avoid single points of failure).
- Keep Backups and Recovery Plans: Maintain off-network backups of site content and DNS zone files, and have a documented incident response plan for domain or site recovery.

Leave a Reply